Description
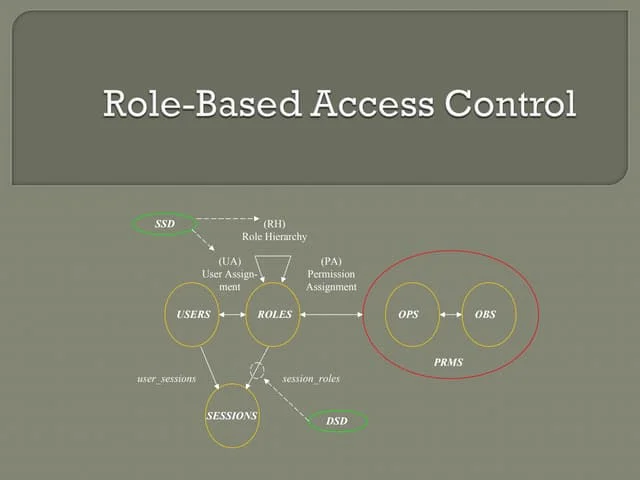
Role-Based Access Control (RBAC) Configuration is an essential security practice that defines permissions based on a user’s role within an organization. By grouping users into roles—such as Admin, Manager, or Analyst—RBAC simplifies access control, enforces least privilege, and ensures operational security across digital systems. Our service starts with a full audit of your organization’s departments, job functions, and system interactions. Based on this, we design a scalable RBAC model with clearly defined roles, responsibilities, and access boundaries. Using tools like Azure Active Directory, AWS IAM, GCP IAM, Linux RBAC, and custom RBAC for applications, we implement fine-grained access policies for each role. Our configurations support hierarchical role structures, policy inheritance, and separation of duties to avoid privilege creep. We also integrate RBAC into your CI/CD pipelines, DevOps tools, and identity governance platforms to support compliance and automation. Our dashboards and reporting features allow security teams to review who has access to what—and why—at any time. Whether you’re deploying RBAC in a startup SaaS app or a global enterprise network, our service brings structure, security, and simplicity to access management.




Ahamed –
“Implementing Role-Based Access Control has significantly streamlined my business operations. Managing permissions was a constant headache before, but now access is secure and efficient. The configuration service was invaluable in setting everything up correctly; it’s made a real difference in how I manage resources and maintain security. It’s been a positive experience and I’m already seeing the benefits.”
Regina –
“Implementing Role-Based Access Control has been transformative for my business. It has streamlined access management, allowing me to focus on growth without worrying about security vulnerabilities. The simplified permissions structure and enforced least privilege have significantly improved our resource access protocols. I am very happy with the service I received and would suggest it to others.”