Description
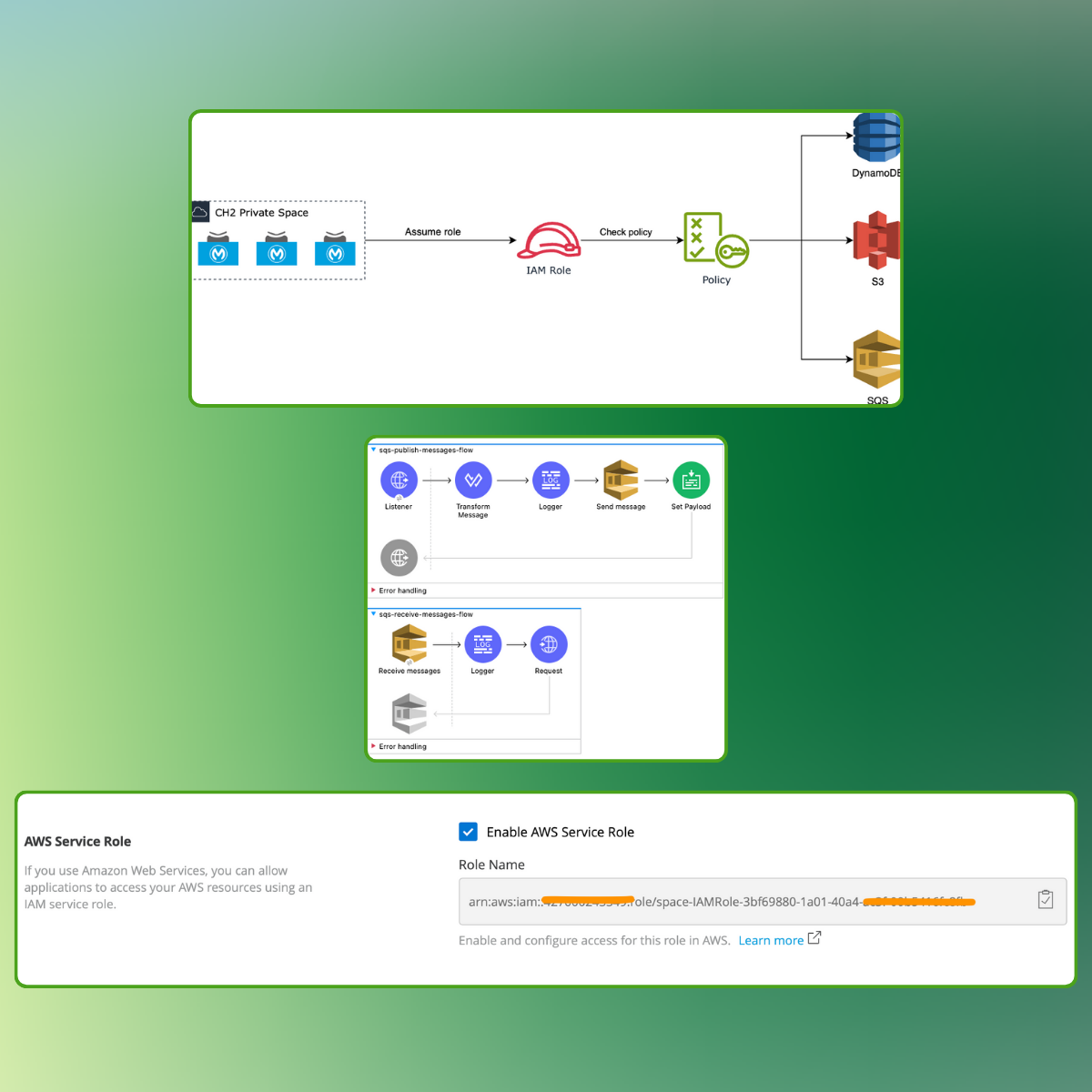
Designing and deploying effective Identity and Access Management (IAM) Policies is critical to maintaining a secure and compliant IT environment. Our service helps organizations define, implement, and manage precise access policies for users, devices, and services across cloud and on-prem infrastructure. Following the Principle of Least Privilege, we ensure each user has the minimal level of access required to perform their job. Our approach begins with a comprehensive assessment of your business structure, regulatory requirements (e.g., HIPAA, GDPR, SOX), and existing role hierarchies. We design policies using role-based, attribute-based, or rule-based access control models depending on your environment and tools—be it AWS IAM, Azure RBAC, GCP IAM, or on-prem AD/LDAP systems. These policies cover account creation, resource permissions, authentication flows, session durations, and escalation approvals. We also implement logging and alerting mechanisms to detect policy violations and unusual access patterns. Our team performs extensive testing to validate that policies enforce expected behaviors without blocking legitimate operations. Whether for infrastructure, applications, APIs, or microservices, we deliver IAM policy frameworks that scale with your business, reduce insider risk, and ensure continuous compliance.




Ismail –
“The IAM policy design and deployment service was invaluable in enhancing my business’s security posture. The tailored policies significantly tightened access control, ensuring compliance and minimizing risk. The results were a secure, auditable environment, delivered effectively.”
Chinwe –
“The IAM policy design and deployment service was instrumental in significantly improving the security posture of my business. The customized policies implemented ensured granular access control, adhering to the principle of least privilege. This resulted in a more secure, compliant, and auditable IT environment, providing me with much-needed peace of mind.”
Ayodeji –
“The IAM Policy Design & Deployment service was instrumental in enhancing my business security. They crafted bespoke IAM policies that gave me fine-grained control over resource access, aligning perfectly with the principle of least privilege. This resulted in a more secure, compliant, and easily auditable IT environment, giving me greater peace of mind and allowing me to focus on growth.”
Afeez –
“These IT services were instrumental in bolstering our security posture through robust IAM policy design and deployment. The customized policies, built on the principle of least privilege, have significantly improved access control across our IT infrastructure, ensuring compliance and making audits far easier. This has not only enhanced security but also streamlined our operational processes.”